Cyberattack risks from email phishing attempts are well-known among healthcare providers and health IT professionals. However, a lesser-known cybersecurity risk stems from the lack of proper digital certificates use, especially but not only, within public and private web-based software.
Digital certificates allow our web browsers to transparently verify the legitimacy of the web sites we connect to. It is key to use valid certificates and manage them properly to provide information systems proof of identity that attackers cannot fake – so that they cannot steal user credentials and personal data, for instance.
Why Are Digital Certificates Important in Healthcare?
Today, as more organizations adopt platforms to integrate their medical devices with clinical systems, it’s important they know which type of digital certificate will work best and be the most manageable – therefore less error prone – to keep sensitive information safe. As stated earlier, digital certificates allow two machines or applications to make sure they are interacting with a genuine counterpart. For example, your web browser will systematically check a server’s certificate if the connection is secure.
This means that each system and web interface a hospital deploys to manage patient data, or configure some patient data related system, should have certificates to constantly prove to the hospital staff they are using a genuine application. It’s a simple way to ensure data like business-sensitive information, user or system credentials, and patient information, is shared securely with a real application, not a fake one deployed as part of an attack to obtain clinical data or credentials.
Exchanging patient data with a spoof application, or allowing a cybercriminal to access patient data using stolen credentials could constitute a data breach as defined by HIPAA. Recovering from such a breach could consume large amounts of financial and labor resources, while damaging the hospital’s reputation and eroding patient confidence.
Apart from cyberattacks, expired digital certificates can also contribute to data errors. For example, in 2020, the security certificate between the California Reportable Disease Information Exchange, known as CalREDIE, and lab company Quest Diagnostics had expired and was not renewed. The expiration delayed the accurate tallying of COVID-19 cases in the state for several days, resulting in a significant undercount before the problem was detected – raising not only health and safety concerns, but also concerns from a public trust perspective.
How to Make the Right Digital Certificate Choices for your Healthcare Organization
Some might think they have data confidentiality covered with encryption only. Encryption is necessary, but insufficient alone. Indeed, when transmitting sensitive data, there are two sweet spots for cyber criminals to steal a copy:
- During data transmission, by eavesdropping – this is where encryption is useful.
- At the destination, typically by impersonating the expected data recipient – You want to have proof of identify of the alleged recipient at the start of the data transmission. Certificates are designed to provide this evidence.
For information systems facing only the members of the organization, it will be easier and cheaper for hospitals to issue their own certificates. There are two options available: self-signed certificates and domain-issued ones. So how do you ensure your healthcare organization is selecting the best digital certificate option? Consider the following:
- Steer Clear of Self-Signed Certificates – Self-signed certificates, which may seem simpler to generate, are not issued by a trusted third-party source and are more difficult for health IT staff to track and manage. They need to be installed individually to each user machine, otherwise users may trust any self-signed certificates, even those that cybercriminals create. This can have negative impacts, as over time users may become accustomed to certificate warning messages that web applications display with such self-signed certificates and inadvertently ignore the alerts that require immediate security breach protocols.
Figure 1: Google Chrome warning on self-signed certificates
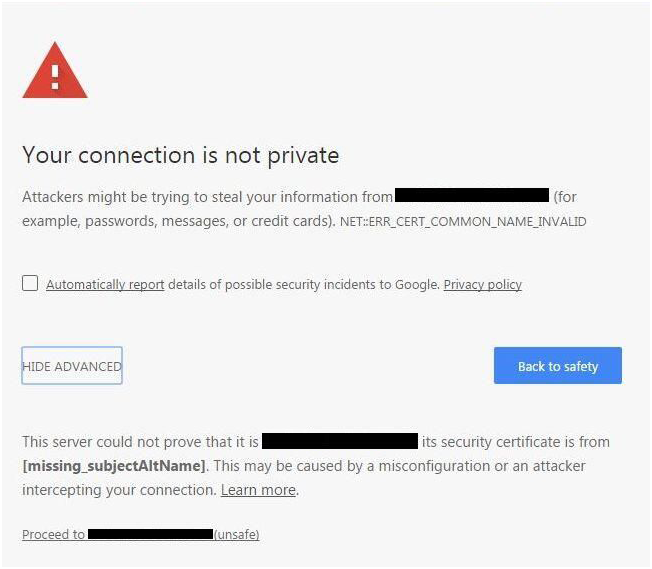
- Look for a Trusted and Manageable Option – Conversely, creating and issuing your own private digital certificate from the organization’s computer domain has several advantages. It enables easier and stronger control of the certificate management by removing the need for changing the list of trusted issuers, the cornerstone of the trust chain for all users in the organization. Therefore, health IT staff do not need to deploy and manage more certificates to many users’ machines as they deploy more internal web applications.
Hospitals in particular are encouraged to have their own Certificate Authority (CA) based on their Windows domain. This gives the foundation for certificate and private key management for any internal system which is facing only other internal systems and/or users. As described above, it is more efficient and secure than disseminating self-signed certificates, and also less expensive than procuring certificate from a CA vendor. Hospitals must also have processes and tools in place to properly manage all certificates, regardless of how they have been issued. Typically, this should allow the renewal of certificates before expiry, enable efficient execution of certificate revocation when something is decommissioned, and provide the ability to regularly check the quality of their certificates and server configuration to ensure certificates are in good standing and that available ciphers are strong enough.
Philips Capsule Supports Customer-Provided Certificates
As a best practice, healthcare organizations should take a hard look at what types of digital certificates are being used enterprise-wide, including certificates for connected medical devices and clinical data receiving systems. We strongly encourage users of Philips Capsule Medical Device Information Platform (MDIP) and Clinical Surveillance to verify that they have created properly signed certificates, typically from their own domain, upon activating each web-based application on their Philips Capsule application servers. This level of customer engagement ensures that certificates are installed and employed, and that update notifications are distributed before certificates expire.
To learn how to create private digital certificates and install them with the Capsule MDIP web applications, ask your Philips Capsule representative for the Capsule Medical Device Information Platform Hardening Guidelines or the Capsule Surveillance Service Manual.
About the author
Christophe Dore is the Product Security Officer of Philips Capsule.
Learn how Philips Capsule Medical Device Information Platform (MDIP) supports interoperability between devices, while safeguarding the data that flows through them.
Download